I seldom use Powerpoint because I am kind of dislike it. I especially dislike the slides made with company’s official templates: if those logos and fancy things are removed, a lot of ink will be saved when printing it. If Powerpoint is not used, all those contents are condensed into a Word or Excel document, a lot of trees will be saved (maybe Powerpoint files are not supposed to be printed out at all, since they are slides, and should be played on the screen with a projector). And this can also save a lot of money for the companies, especially in such a bad economy.
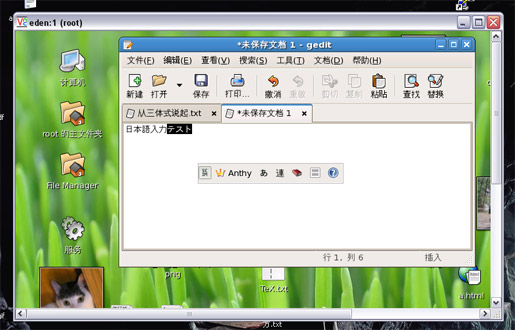
Today, when I tried to use Powerpoint 2007 at home for the FIRST time (I even hesitated if I should have installed it or not when I installed Office 2007), I was astonished that I cannot type Chinese in it! Nor Japanese can be input. But if I type some Chinese characters into a text editor, and do a copy-and-paste, it shows in Powerpoint properly.
According to some investigations via internet, it seems to be caused by a Windows XP update. BTW, my Office 2007 was installed in Windows XP, I don’t have later versions of Windows at hand, so I am not sure if this applies to other Windows or not.
The fix is relatively straightforward, but the Registry should be modified. I made a .reg file for this. Just right click on it and choose “Merge” in popup menu. It takes effect at once without restarting Windows or Powerpoint. It works for both Chinese and Japanese input (I guess it may also work for other languages such as Korean but I am not sure). But this is totally at your own risk, ie. I won’t be responsible for any damages caused by using this file. So if you want to use this, please backup the Registry first (I didn’t though).